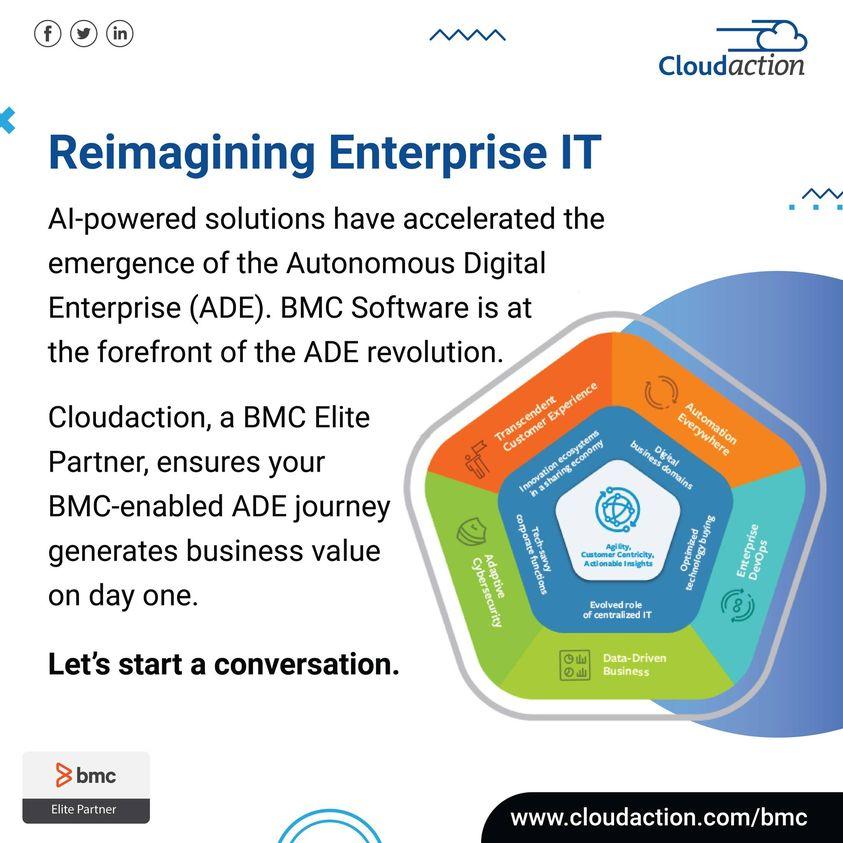
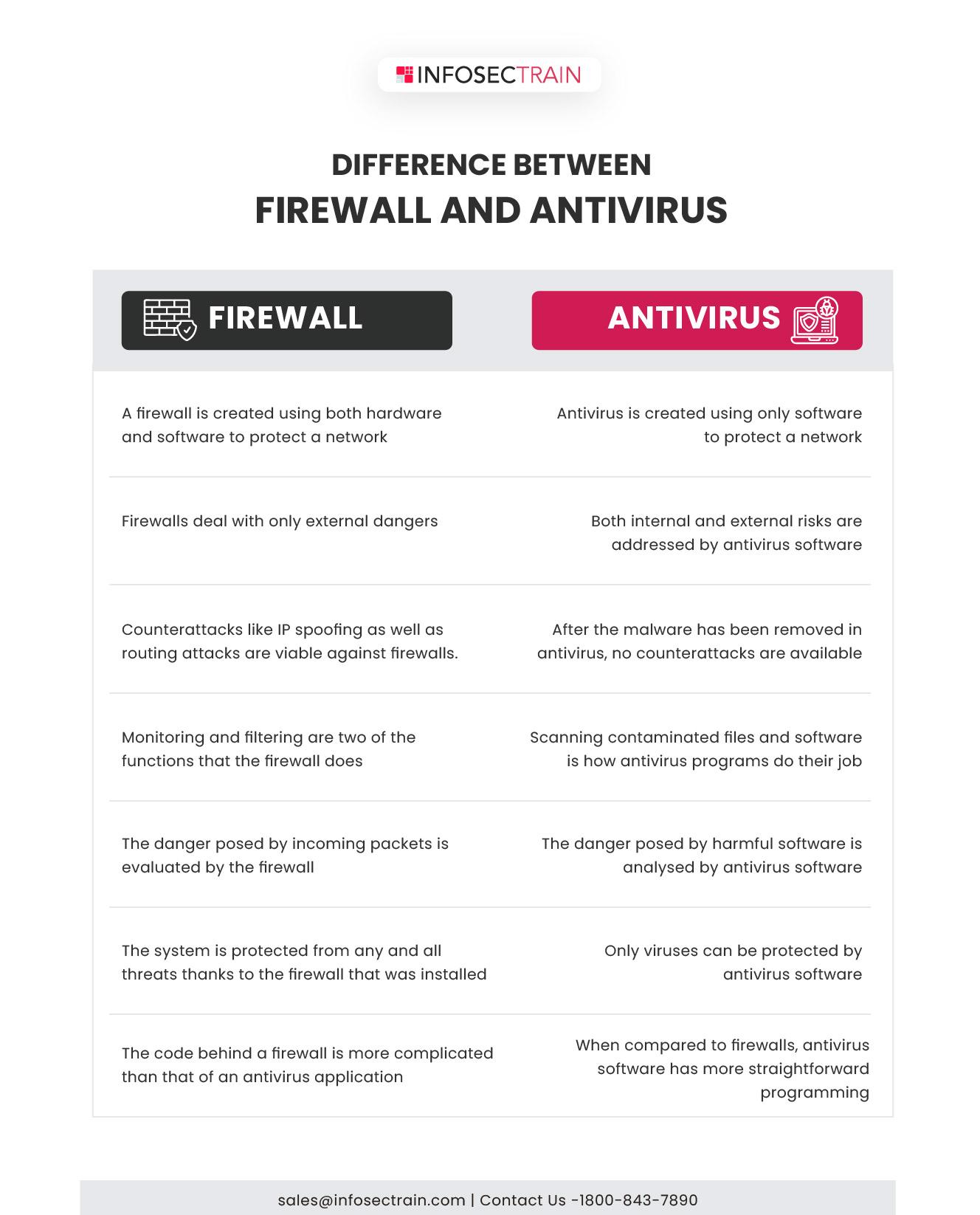
86 Inch Interactive Whiteboard manufacturers Overview: Touch Screen Interactive Whiteboard is an all-in-one device, such as: computer, whiteboard, etc., making your meetings more concise and efficient. Infrared high-sensitivity touch panel realizes a precious writing. It supports one-click screen projection of different devices which offers a more flexible operation. Video conference and remote assistance break space restrictions. Besides, screen-sharing completes meeting decisions anytime and anywhere. HD display screen is able to show every image details, screen hardness reaches the level of anti-scratch. Touch Screen Interactive Whiteboard supports both Android and Windows systems, and is compatible with various software to enhance your meeting experience. Excellent performance and remote collaboration allows your meeting partners to easily modify files, it also can be used in classrooms like free annotations and clear explanations. Ultra-thin bezel is stylish and concise and at the same time brings you a perfect visual experience, anti-glare technology ensures the image clarity, even in brighter environments. Free and boundless collaboration Ultra-HD display | Remote Collaboration | Intelligent Writing | Interactive Mirroring | Extraordinary Performance Slim bezel, Large vision, Sharp display 4K Ultra HD large display with slim bezel on double sides deliver wider vision and better immersive experience. Anti-glare technology assures the sharpness of imagines, even in the bright environment. Integrated and light assembly, easy remote sharing Integrated design, built-in camera, voice picking-up, and speaker modules. Outstanding configuration is specially designed for multi-parties HD video conference Leading technology, applied for presenting more fluent, clear, and stable audio and video experiences, includes 8-megapixel camera, 6 built-in array microphones, 8m voice picking-up*, 2.1 channel stereo, and real human voice restored by intelligent EQ. 8-megapixel68m2.1 camerabuilt-in array microphonesvoice picking-upchannel stereo Remote collaboration Eliminates the space limitation Extraordinary performance, excellent quality Equipped with 7th Gen Intel Core TM processors, the interactive boards have strong performance and reliability, support Android 8.0 / Windows 10 dual-system, and up to 16GB DDR4-RAM. It is also compatible with various applications. Easy operating creates efficient meetings.86 Inch Interactive Whiteboard manufacturers website:
http://www.tyaluxmonitors.com/interactive-whiteboard/86-inch-interactive-whiteboard/86 Inch Interactive Whiteboard manufacturers Overview: Touch Screen Interactive Whiteboard is an all-in-one device, such as: computer, whiteboard, etc., making your meetings more concise and efficient. Infrared high-sensitivity touch panel realizes a precious writing. It supports one-click screen projection of different devices which offers a more flexible operation. Video conference and remote assistance break space restrictions. Besides, screen-sharing completes meeting decisions anytime and anywhere. HD display screen is able to show every image details, screen hardness reaches the level of anti-scratch. Touch Screen Interactive Whiteboard supports both Android and Windows systems, and is compatible with various software to enhance your meeting experience. Excellent performance and remote collaboration allows your meeting partners to easily modify files, it also can be used in classrooms like free annotations and clear explanations. Ultra-thin bezel is stylish and concise and at the same time brings you a perfect visual experience, anti-glare technology ensures the image clarity, even in brighter environments. Free and boundless collaboration Ultra-HD display | Remote Collaboration | Intelligent Writing | Interactive Mirroring | Extraordinary Performance Slim bezel, Large vision, Sharp display 4K Ultra HD large display with slim bezel on double sides deliver wider vision and better immersive experience. Anti-glare technology assures the sharpness of imagines, even in the bright environment. Integrated and light assembly, easy remote sharing Integrated design, built-in camera, voice picking-up, and speaker modules. Outstanding configuration is specially designed for multi-parties HD video conference Leading technology, applied for presenting more fluent, clear, and stable audio and video experiences, includes 8-megapixel camera, 6 built-in array microphones, 8m voice picking-up*, 2.1 channel stereo, and real human voice restored by intelligent EQ. 8-megapixel68m2.1 camerabuilt-in array microphonesvoice picking-upchannel stereo Remote collaboration Eliminates the space limitation Extraordinary performance, excellent quality Equipped with 7th Gen Intel Core TM processors, the interactive boards have strong performance and reliability, support Android 8.0 / Windows 10 dual-system, and up to 16GB DDR4-RAM. It is also compatible with various applications. Easy operating creates efficient meetings.86 Inch Interactive Whiteboard manufacturers website:http://www.tyaluxmonitors.com/interactive-whiteboard/86-inch-interactive-whiteboard/