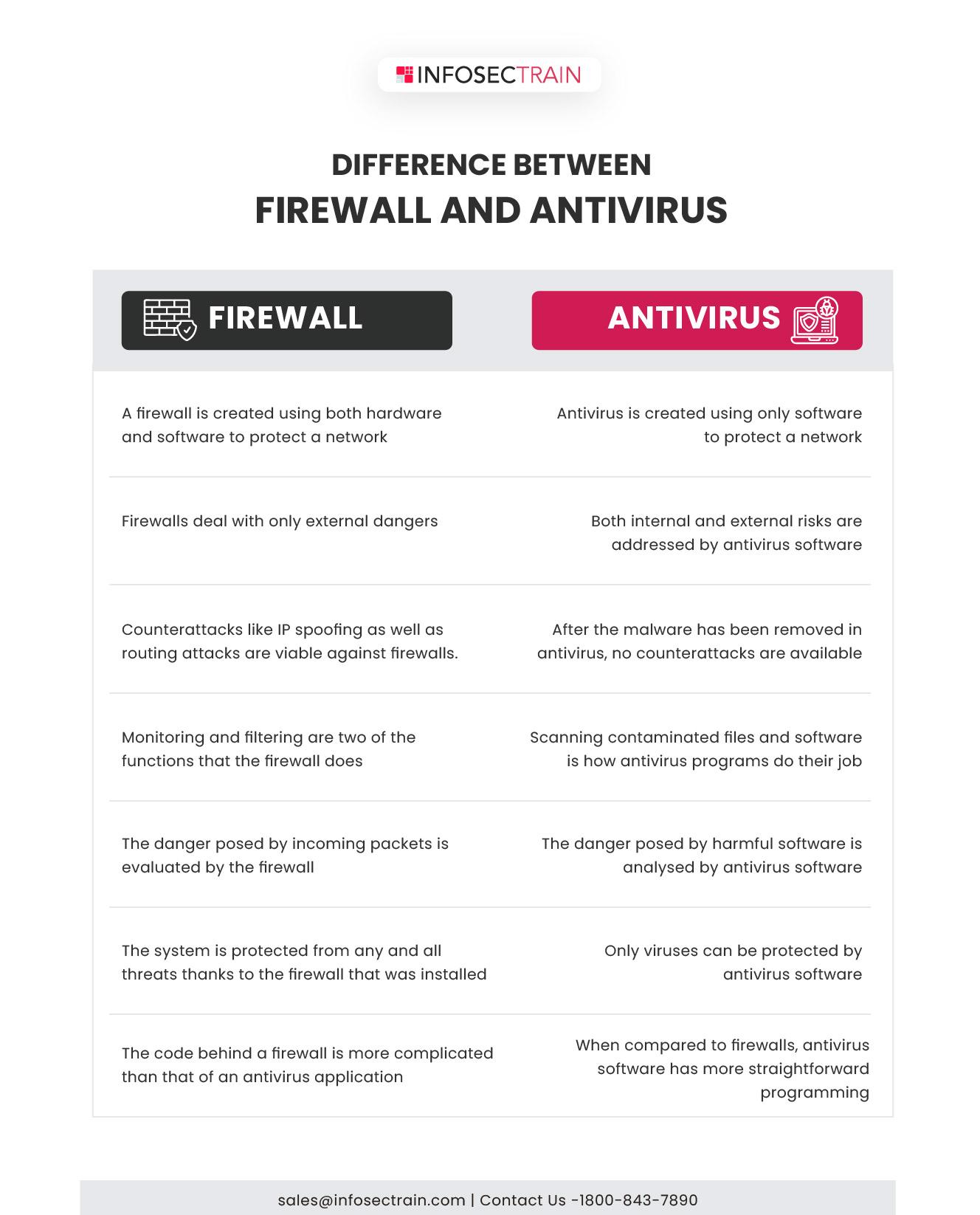
Fuzz Testing Steps
Fuzz testing, often called fuzzing, is a software testing technique used to identify vulnerabilities and flaws in computer programs, specifically in software applications, operating systems, and network protocols. The technique involves sending intentionally malformed or random data inputs to a target program to observe its response. The primary objective of fuzz testing is to detect security vulnerabilities, unforeseen behavior, system failures, stability concerns, or any other anomalies inside the targeted software.
Read Here: https://medium.com/@Infosec-Train/what-is-fuzz-testing-340bb1c94a4c
#FuzzTestingSteps #SoftwareTesting #SecurityTesting #QualityAssurance #InfoSecInsights #CyberSecQA #FuzzTesting #TestAutomation #SoftwareQuality #BugHunting #SecurityQA #SoftwareEngineering #InfoSecAwareness #CyberSecurityTesting #QualityEngineering #infosectrain #learntorise
Fuzz testing, often called fuzzing, is a software testing technique used to identify vulnerabilities and flaws in computer programs, specifically in software applications, operating systems, and network protocols. The technique involves sending intentionally malformed or random data inputs to a target program to observe its response. The primary objective of fuzz testing is to detect security vulnerabilities, unforeseen behavior, system failures, stability concerns, or any other anomalies inside the targeted software.
Read Here: https://medium.com/@Infosec-Train/what-is-fuzz-testing-340bb1c94a4c
#FuzzTestingSteps #SoftwareTesting #SecurityTesting #QualityAssurance #InfoSecInsights #CyberSecQA #FuzzTesting #TestAutomation #SoftwareQuality #BugHunting #SecurityQA #SoftwareEngineering #InfoSecAwareness #CyberSecurityTesting #QualityEngineering #infosectrain #learntorise
Fuzz Testing Steps
Fuzz testing, often called fuzzing, is a software testing technique used to identify vulnerabilities and flaws in computer programs, specifically in software applications, operating systems, and network protocols. The technique involves sending intentionally malformed or random data inputs to a target program to observe its response. The primary objective of fuzz testing is to detect security vulnerabilities, unforeseen behavior, system failures, stability concerns, or any other anomalies inside the targeted software.
Read Here: https://medium.com/@Infosec-Train/what-is-fuzz-testing-340bb1c94a4c
#FuzzTestingSteps #SoftwareTesting #SecurityTesting #QualityAssurance #InfoSecInsights #CyberSecQA #FuzzTesting #TestAutomation #SoftwareQuality #BugHunting #SecurityQA #SoftwareEngineering #InfoSecAwareness #CyberSecurityTesting #QualityEngineering #infosectrain #learntorise
0 Comentários
0 Compartilhamentos