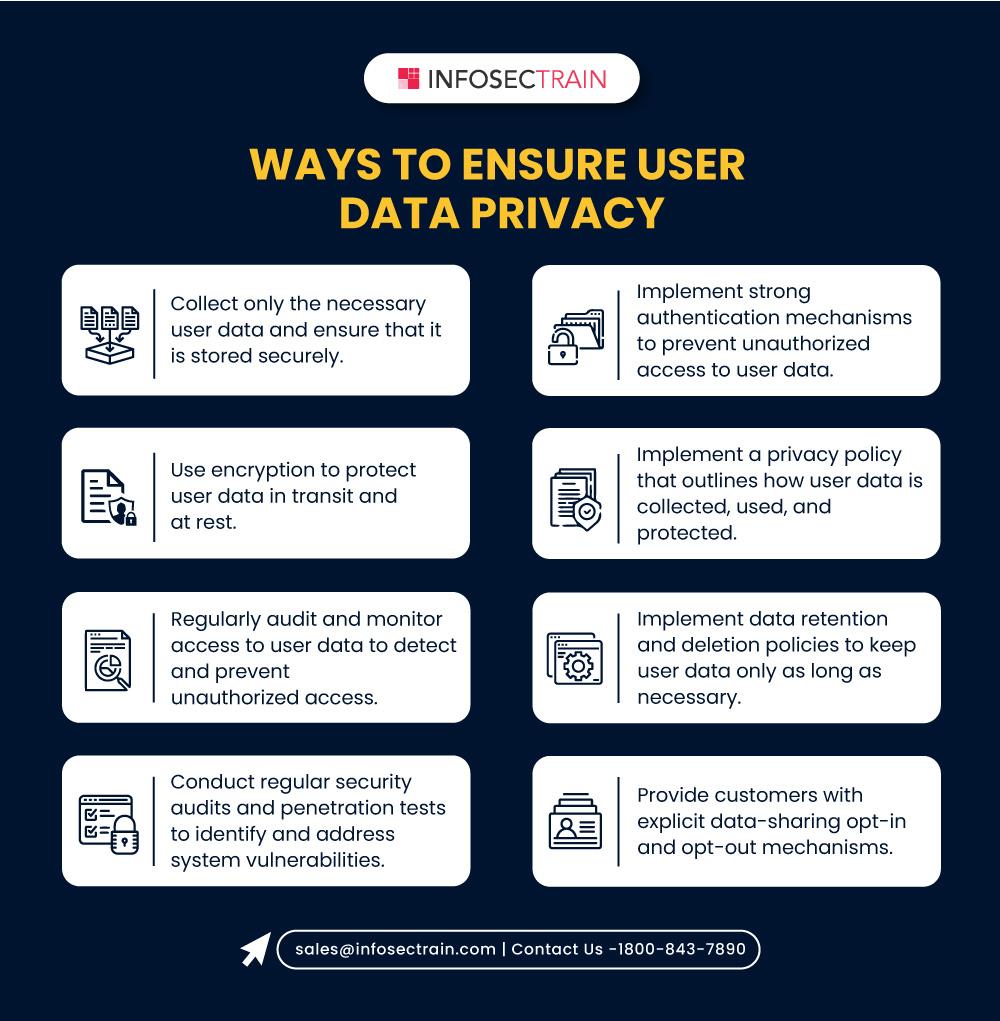
Compliance and Regulatory Updates for 2024
The introduction of enhanced data protection regulations has reshaped the global data privacy landscape, with an emphasis on protecting individuals' privacy rights. Regions have seen updates to existing data privacy laws, such as the expansion of the California Consumer Privacy Act (CCPA) and updates to the EU's General Data Protection Regulation (GDPR).
Read more: https://infosec-train.blogspot.com/2024/03/compliance-and-regulatory-updates-for-2024.html
#Compliance2024 #RegulatoryUpdates #ComplianceTrends #RegulatoryCompliance #RegulatoryChanges #ComplianceManagement #RegulatoryGuidelines #ComplianceStandards #RegulatoryRequirements #ComplianceUpdates #infosectrain #learntorise
The introduction of enhanced data protection regulations has reshaped the global data privacy landscape, with an emphasis on protecting individuals' privacy rights. Regions have seen updates to existing data privacy laws, such as the expansion of the California Consumer Privacy Act (CCPA) and updates to the EU's General Data Protection Regulation (GDPR).
Read more: https://infosec-train.blogspot.com/2024/03/compliance-and-regulatory-updates-for-2024.html
#Compliance2024 #RegulatoryUpdates #ComplianceTrends #RegulatoryCompliance #RegulatoryChanges #ComplianceManagement #RegulatoryGuidelines #ComplianceStandards #RegulatoryRequirements #ComplianceUpdates #infosectrain #learntorise
Compliance and Regulatory Updates for 2024
The introduction of enhanced data protection regulations has reshaped the global data privacy landscape, with an emphasis on protecting individuals' privacy rights. Regions have seen updates to existing data privacy laws, such as the expansion of the California Consumer Privacy Act (CCPA) and updates to the EU's General Data Protection Regulation (GDPR).
Read more: https://infosec-train.blogspot.com/2024/03/compliance-and-regulatory-updates-for-2024.html
#Compliance2024 #RegulatoryUpdates #ComplianceTrends #RegulatoryCompliance #RegulatoryChanges #ComplianceManagement #RegulatoryGuidelines #ComplianceStandards #RegulatoryRequirements #ComplianceUpdates #infosectrain #learntorise
0 Reacties
0 aandelen
487 Views
0 voorbeeld