Promoted Posts
Please log in to like, share and comment!
-
-
Why Every Student Should Join a Global Online CommunityIn today’s digital world, learning is no longer limited to classrooms or campuses. Students now have the opportunity to connect with peers from different countries, cultures, and academic backgrounds through a global student network. Joining an online student community can open doors to collaboration, knowledge sharing, and career opportunities that may not be available within a...0 Comments 0 Shares 2K Views 0 Reviews
-
-
0 Comments 0 Shares 1K Views 0 Reviews
-
Third-Party Risk Management (TPRM): How to Assess Vendor Security
Most organizations invest heavily in securing their own environments. Firewalls are configured, identities are locked down, and incident response plans are rehearsed. Yet many of the most damaging breaches don’t start internally. They start with a trusted third party.
Read More: https://azpirantz.com/blog/third-party-risk-management-tprm-how-to-assess-vendor-security/
#VendorSecurity #CyberSecurity #RiskManagement #VendorAssessmentThird-Party Risk Management (TPRM): How to Assess Vendor Security Most organizations invest heavily in securing their own environments. Firewalls are configured, identities are locked down, and incident response plans are rehearsed. Yet many of the most damaging breaches don’t start internally. They start with a trusted third party. Read More: https://azpirantz.com/blog/third-party-risk-management-tprm-how-to-assess-vendor-security/ #VendorSecurity #CyberSecurity #RiskManagement #VendorAssessment AZPIRANTZ.COMThird-Party Risk Management (TPRM): How to Assess Vendor SecurityLearn how to assess vendor security with a strong Third-Party Risk Management (TPRM) framework and reduce enterprise risk.0 Comments 0 Shares 2K Views 0 Reviews
AZPIRANTZ.COMThird-Party Risk Management (TPRM): How to Assess Vendor SecurityLearn how to assess vendor security with a strong Third-Party Risk Management (TPRM) framework and reduce enterprise risk.0 Comments 0 Shares 2K Views 0 Reviews -
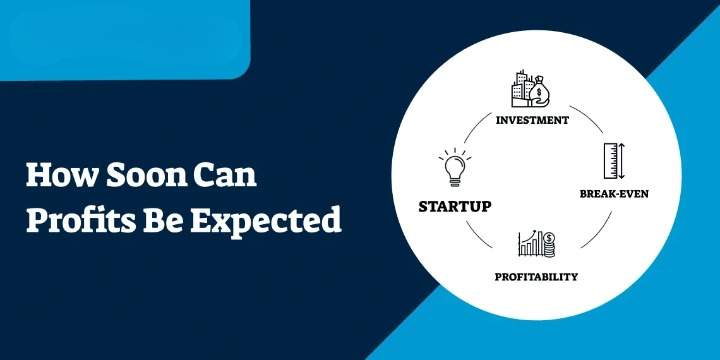
Small Business Success Timeline: How Soon Can Profits Be Expected?
A profitable business earns more revenue than its operational costs and expenses, and making a profit is the aim of many small business owners.
For those who operate a small business, their primary aim is to generate profits quickly. Business owners prefer not to wait for a long period to earn profits once the business begins. Everybody loves quick profits, especially in a shorter period. But when does a small business attain the expected profits?
Tap the link, to learn more
https://www.invoicetemple.com
#online invoicing software #best inventory management software #invoicesSmall Business Success Timeline: How Soon Can Profits Be Expected? A profitable business earns more revenue than its operational costs and expenses, and making a profit is the aim of many small business owners. For those who operate a small business, their primary aim is to generate profits quickly. Business owners prefer not to wait for a long period to earn profits once the business begins. Everybody loves quick profits, especially in a shorter period. But when does a small business attain the expected profits? Tap the link, to learn more https://www.invoicetemple.com #online invoicing software #best inventory management software #invoices0 Comments 0 Shares 2K Views 0 Reviews -
0 Comments 0 Shares 1K Views 0 Reviews
-
Build a Career with BSc in Animation and VFX
Turn your creativity into a professional qualification with a BSc in animation and VFX designed for today’s entertainment industry. This degree program covers advanced rendering, CGI pipelines, and motion graphics, supported by expert faculty from a reputed animation institute. Alongside vfx training courses and practical 3D animation course exposure, students develop portfolios that attract top recruiters. It’s the perfect blend of art and technology for aspiring animators and VFX artists.
👉Discover more here -https://moopleanimationinstitute.blogspot.com/2026/03/BSc-in-3D-Animation-and-VFX.html
📞Call us - +91 81009 82727
#BScinanimationandVFX #animationcollege #VFXdegree #3Danimationtraining #multimediacourse #filmproduction
Build a Career with BSc in Animation and VFX Turn your creativity into a professional qualification with a BSc in animation and VFX designed for today’s entertainment industry. This degree program covers advanced rendering, CGI pipelines, and motion graphics, supported by expert faculty from a reputed animation institute. Alongside vfx training courses and practical 3D animation course exposure, students develop portfolios that attract top recruiters. It’s the perfect blend of art and technology for aspiring animators and VFX artists. 👉Discover more here -https://moopleanimationinstitute.blogspot.com/2026/03/BSc-in-3D-Animation-and-VFX.html 📞Call us - +91 81009 82727 #BScinanimationandVFX #animationcollege #VFXdegree #3Danimationtraining #multimediacourse #filmproduction0 Comments 0 Shares 3K Views 0 Reviews -
0 Comments 0 Shares 1K Views 0 Reviews
-
-
Palxup on Play Store 👉 https://bit.ly/4cl5H7APalxup on Play Store 👉 https://bit.ly/4cl5H7A0 Comments 0 Shares 3K Views 0 Reviews
-
Business Continuity & Disaster Recovery (BCMS) Essentials
Disruptions are no longer unusual events. Cyberattacks, cloud outages, supplier failures, natural incidents, and simple operational mistakes can interrupt business with little warning. What consistently separates resilient organizations from the rest is not the absence of incidents, but the ability to respond calmly and recover in a controlled manner.
Read More: https://azpirantz.com/blog/business-continuity-disaster-recovery-bcms-essentials/
#BCMS #BusinessContinuity #DisasterRecovery #BCDRBusiness Continuity & Disaster Recovery (BCMS) Essentials Disruptions are no longer unusual events. Cyberattacks, cloud outages, supplier failures, natural incidents, and simple operational mistakes can interrupt business with little warning. What consistently separates resilient organizations from the rest is not the absence of incidents, but the ability to respond calmly and recover in a controlled manner. Read More: https://azpirantz.com/blog/business-continuity-disaster-recovery-bcms-essentials/ #BCMS #BusinessContinuity #DisasterRecovery #BCDR AZPIRANTZ.COMBusiness Continuity & Disaster Recovery (BCMS) EssentialsA practical guide to Business Continuity and Disaster Recovery (BCMS) for minimizing downtime and managing crises.0 Comments 0 Shares 5K Views 0 Reviews
AZPIRANTZ.COMBusiness Continuity & Disaster Recovery (BCMS) EssentialsA practical guide to Business Continuity and Disaster Recovery (BCMS) for minimizing downtime and managing crises.0 Comments 0 Shares 5K Views 0 Reviews
More Stories