Cyber Security Tips for Small Businesses
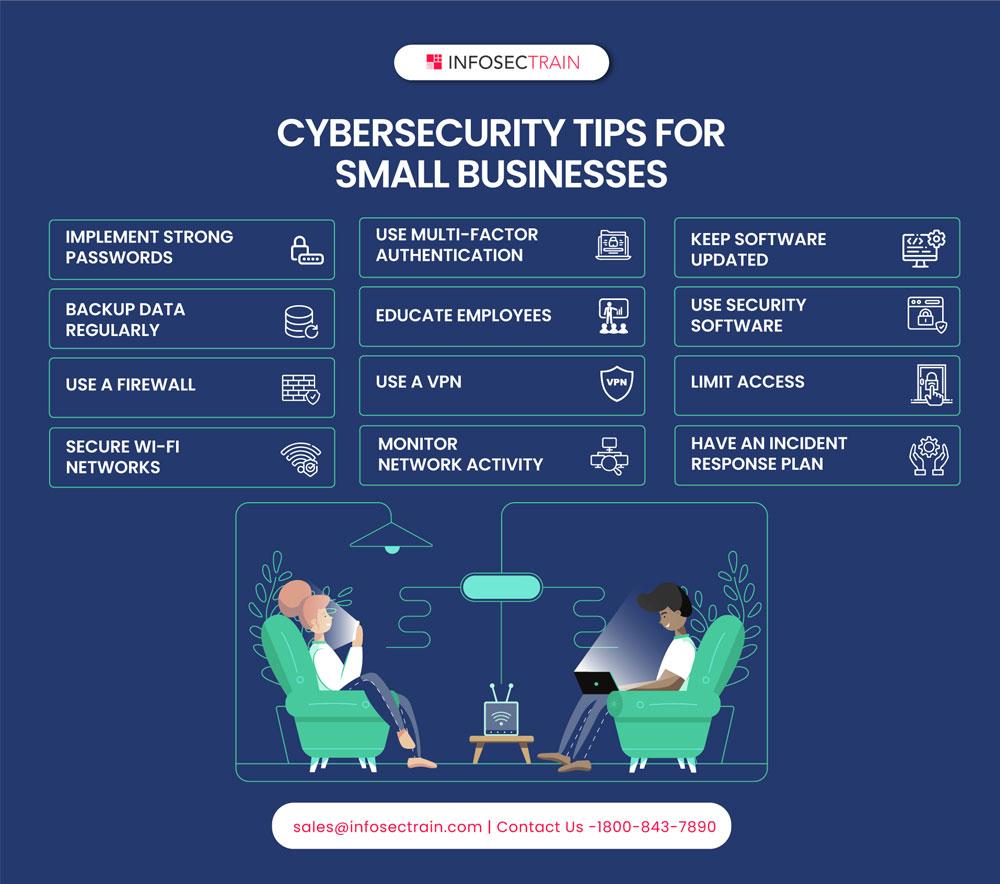
1. Employee Training and Awareness:
Educate your employees about cybersecurity best practices, such as recognizing phishing emails, creating strong passwords, and being cautious about sharing sensitive information.
2. Implement Strong Access Controls:
Enforce the principle of least privilege by providing employees with access only to the systems and data necessary for their roles. Implement multi-factor authentication (MFA) for an added layer of security.
3. Regular Software Updates and Patch Management:
Ensure that all software, including operating systems and applications, is up to date with the latest security patches to address vulnerabilities that could be exploited by cybercriminals.
4. Secure Network Configuration:
Secure your Wi-Fi network with a strong password, and consider using WPA2 or WPA3 encryption. Implement a firewall and consider segmenting your network to isolate sensitive data and critical systems.
Free cybersecurity training, Register Here: https://www.infosectrain.com/free-cybersecurity-training/
#SmallBizSecurity #CyberSecurityTips #InfoSecSmallBiz #SmallBusinessProtection #CyberSafety #InfoSecAwareness #SmallBizCyber #CyberSecForSmallBiz #BusinessProtection #SmallBizTech #CyberSecTips #InfoSecTips #SmallBusinessSecurity #CyberAwareness #infosectrain #learntorise
1. Employee Training and Awareness:
Educate your employees about cybersecurity best practices, such as recognizing phishing emails, creating strong passwords, and being cautious about sharing sensitive information.
2. Implement Strong Access Controls:
Enforce the principle of least privilege by providing employees with access only to the systems and data necessary for their roles. Implement multi-factor authentication (MFA) for an added layer of security.
3. Regular Software Updates and Patch Management:
Ensure that all software, including operating systems and applications, is up to date with the latest security patches to address vulnerabilities that could be exploited by cybercriminals.
4. Secure Network Configuration:
Secure your Wi-Fi network with a strong password, and consider using WPA2 or WPA3 encryption. Implement a firewall and consider segmenting your network to isolate sensitive data and critical systems.
Free cybersecurity training, Register Here: https://www.infosectrain.com/free-cybersecurity-training/
#SmallBizSecurity #CyberSecurityTips #InfoSecSmallBiz #SmallBusinessProtection #CyberSafety #InfoSecAwareness #SmallBizCyber #CyberSecForSmallBiz #BusinessProtection #SmallBizTech #CyberSecTips #InfoSecTips #SmallBusinessSecurity #CyberAwareness #infosectrain #learntorise
Cyber Security Tips for Small Businesses
1. Employee Training and Awareness:
Educate your employees about cybersecurity best practices, such as recognizing phishing emails, creating strong passwords, and being cautious about sharing sensitive information.
2. Implement Strong Access Controls:
Enforce the principle of least privilege by providing employees with access only to the systems and data necessary for their roles. Implement multi-factor authentication (MFA) for an added layer of security.
3. Regular Software Updates and Patch Management:
Ensure that all software, including operating systems and applications, is up to date with the latest security patches to address vulnerabilities that could be exploited by cybercriminals.
4. Secure Network Configuration:
Secure your Wi-Fi network with a strong password, and consider using WPA2 or WPA3 encryption. Implement a firewall and consider segmenting your network to isolate sensitive data and critical systems.
Free cybersecurity training, Register Here: https://www.infosectrain.com/free-cybersecurity-training/
#SmallBizSecurity #CyberSecurityTips #InfoSecSmallBiz #SmallBusinessProtection #CyberSafety #InfoSecAwareness #SmallBizCyber #CyberSecForSmallBiz #BusinessProtection #SmallBizTech #CyberSecTips #InfoSecTips #SmallBusinessSecurity #CyberAwareness #infosectrain #learntorise
0 Comentários
0 Compartilhamentos